Researchers at Southern Methodist University have[1] examined[2] how common video conferencing services react to short bursts of sound that travel through the normal two-way audio channel. They focused on platforms that millions use each day, including Zoom and Microsoft Teams, and they found that a determined participant could identify where another person is located with high reliability. That ability does not require hacking the target’s computer or access to hidden malware. It only depends on what is already allowed inside every meeting: a brief moment of sound.
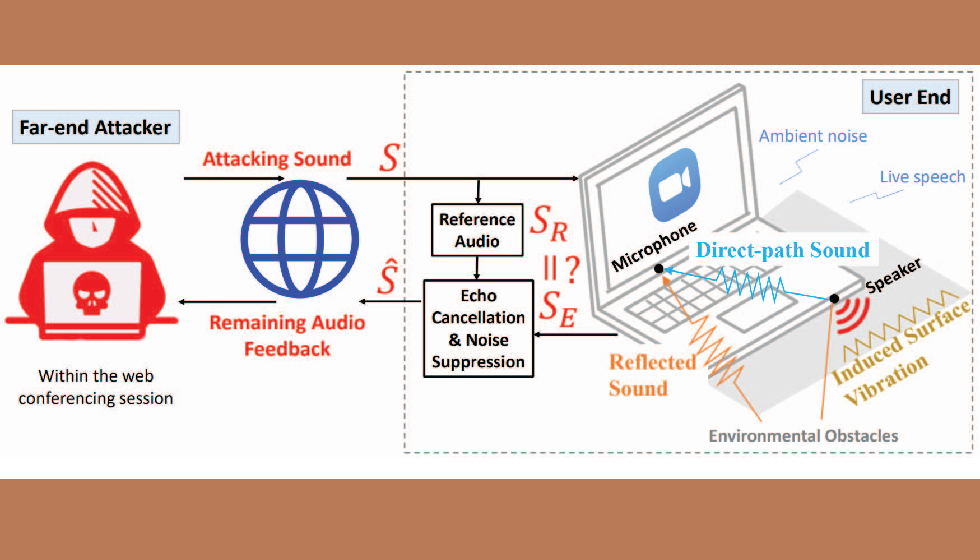
The issue exists because of the way audio behaves indoors. When a loudspeaker emits a noise, parts of that noise bounce around and return to the microphone as tiny echoes. Those echoes carry information about walls, furniture, ceiling height, room size, and even the presence of objects such as shelves or curtains. The study demonstrated that these patterns form a kind of acoustic fingerprint that reflects the user’s surroundings. If someone inserts a probing sound into the call, software can analyze the echo patterns and compare them with data learned earlier from different environments. This is known academically as remote acoustic sensing.
The team designed two forms of attack that rely on this mechanism. In one case, the probing signals travel directly within the conversation channel and try to bypass echo suppression features designed to improve audio clarity. In the second case, the attacker hides the probing sound inside everyday notifications or other audio played through the call. Those small noises often appear during meetings when calendar reminders pop up or when a message reaches someone’s device. The software uses intelligent processing to extract useful spatial details from the faint reflections that return after these sounds occur.
During six months of experiments, the researchers captured data from settings that included homes, offices, hotel rooms, and even cars. They then tested whether a system could distinguish a location the user had visited before or classify new unfamiliar places into broad environment types. The accuracy reached nearly eighty nine percent on both tasks when only a single short probing sound was available. That success rate signals a strong potential for misuse, because a spy or thief could learn whether someone participates from their house or workplace. The information might reveal patterns of daily movement over time.
A surprising finding concerns the moments when people speak. Modern videoconferencing software suppresses ambient noise when users remain silent, in order to reduce distraction. However, when a participant begins talking, the suppression relaxes to preserve their voice. This unintentional behavior also strengthens the attacker’s probing signal, making the returning echoes cleaner. People often leave a short margin before and after speaking to avoid clipping their sentences. Those pauses form windows of opportunity even for cautious users who press mute after every comment.
The noises involved can be extremely brief. Some experiments used bursts only one tenth of a second long, which hides them easily inside the natural motion of a conversation. Most users would not notice anything unusual, and nothing appears visually suspicious on the screen. Virtual backgrounds do not provide any protection because the attack does not rely on the camera at all.
The group behind this work is now exploring ways to protect users against such privacy risks. One idea is that servers handling the audio could detect probing attempts and discard suspicious portions before sending them along to meeting participants. However, building a complete defense remains difficult. Any solution must avoid degrading the quality of legitimate voices and must adapt quickly as attackers change their strategies.
Acoustic fingerprints exist because sound naturally interacts with enclosed spaces. That fact will not change. The findings suggest that people should remain aware that muting a microphone does not fully eliminate exposure. While the everyday threat level may be low right now, the research highlights a new category of privacy concerns emerging from ordinary communication tools that millions rely on without giving much thought to the hidden signals their rooms may reveal.
Notes: This post was edited/created using GenAI tools.
Read next: AI Is Changing Software Shopping and Reddit Wants to Lead the Shift[3]