A large share of satellite data moving above North America has been found unprotected, exposing communications from mobile carriers, corporations, and even military networks. The discovery came from a joint investigation by researchers at the University of California, San Diego, and the University of Maryland, who spent seven months scanning the sky with low-cost satellite equipment.
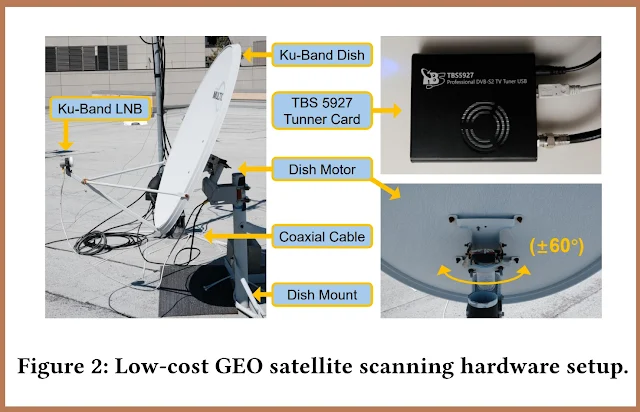
The team examined signals from 39 geostationary satellites and 411 transponders visible from La Jolla, California, using a consumer-grade motorized dish and custom-built software that cost under $800.
Their scans revealed that about half of all links to high-orbit satellites were transmitting data in cleartext, leaving large volumes of voice calls, text messages, and operational data accessible to anyone with similar hardware.
How the discovery happened
The researchers[1] built an automated ground station capable of aligning to each satellite and decoding raw traffic. By developing a universal parser that could handle seven different and often proprietary communication stacks, they overcame a major obstacle that limited earlier studies. This allowed them to recover six times more data packets than previous research tools could handle.
Across their recordings, they found that link-layer encryption, long used in satellite television, was rarely enabled for internet or private network connections. Many organizations treated satellite backhaul as an internal network path, assuming the signal was secure by nature of being in space. Instead, the study showed that such signals could be intercepted from Earth with off-the-shelf equipment.
What the researchers uncovered
The investigation exposed unencrypted traffic from a range of industries and government bodies. Telecommunications companies were among the first identified. In one case, the team intercepted T-Mobile cellular backhaul data from rural tower links, including unprotected text messages, call metadata, and voice data sent through the IP Multimedia Subsystem. T-Mobile confirmed the finding and stated that the problem affected less than 0.1% of its remote sites. Encryption has since been applied.
Similar unencrypted traffic was found from AT&T Mexico, which revealed control signals and internet sessions routed through its satellite backhaul. Another carrier, KPU Telecommunications in Alaska, was found to be transmitting unencrypted VoIP data during backup link operation.
Beyond telecom systems, the team recorded internal communications from major companies and institutions. Walmart-Mexico’s satellite links exposed login credentials, inventory records, and internal email traffic. Grupo Santander, Banorte, and Banjército were also affected, with plaintext LDAP and ATM network data visible across satellite channels. The researchers traced these signals through identifiable IP ranges and organizational domains.
Government and military exposure
The analysis also uncovered sensitive government transmissions. Two Mexican government and military links were found to be broadcasting unencrypted operational data, including personnel files, military asset locations, and live surveillance records. Some traffic even contained web application data related to law enforcement and narcotics tracking systems.
From another satellite, the researchers intercepted communication originating from U.S. military vessels. That traffic included plaintext DNS and SIP signaling data, which identified ship names that matched known naval assets. While some encryption was present in isolated links, several channels still carried unencrypted packets mixed with ordinary network traffic.
Why encryption is missing
The study found that the lack of encryption was not due to technical limits. Most satellite terminals and hubs include encryption options at the physical, link, or network layer. In practice, many organizations disable it to save bandwidth, reduce latency, or avoid troubleshooting difficulties. In some cases, encryption licenses for satellite systems carry extra costs, leading operators to rely on trust in isolation rather than protection.
Another factor is operational inertia. Satellite systems often run for years without full audits, and responsibility for encryption can shift between providers, resellers, and end users. As a result, critical communications (covering everything from industrial control systems to financial data) remain open to interception.
Broader implications
The researchers disclosed their findings between December 2024 and mid-2025 to affected organizations, including T-Mobile, AT&T, Intelsat, Panasonic Avionics, and several government agencies. Many have since applied fixes, but not all. The study warns that the same patterns likely exist beyond North America, given that the same satellite equipment and protocols are used globally.
The team has made its scanning tools publicly available to encourage independent verification and stronger encryption adoption. They note that while low-Earth orbit networks like Starlink already employ modern cryptographic frameworks, traditional geostationary links remain a significant blind spot in network security… one that sits quietly above most of the planet.
Notes: This post was edited/created using GenAI tools.
Read next:
• How Technical Glitches Quietly Drain U.S. Developer Productivity[2]
• The Truth About Dopamine Detoxes: Can You Really Reset Your Brain?[3]
References
- ^ The researchers (satcom.sysnet.ucsd.edu)
- ^ How Technical Glitches Quietly Drain U.S. Developer Productivity (www.digitalinformationworld.com)
- ^ The Truth About Dopamine Detoxes: Can You Really Reset Your Brain? (www.digitalinformationworld.com)