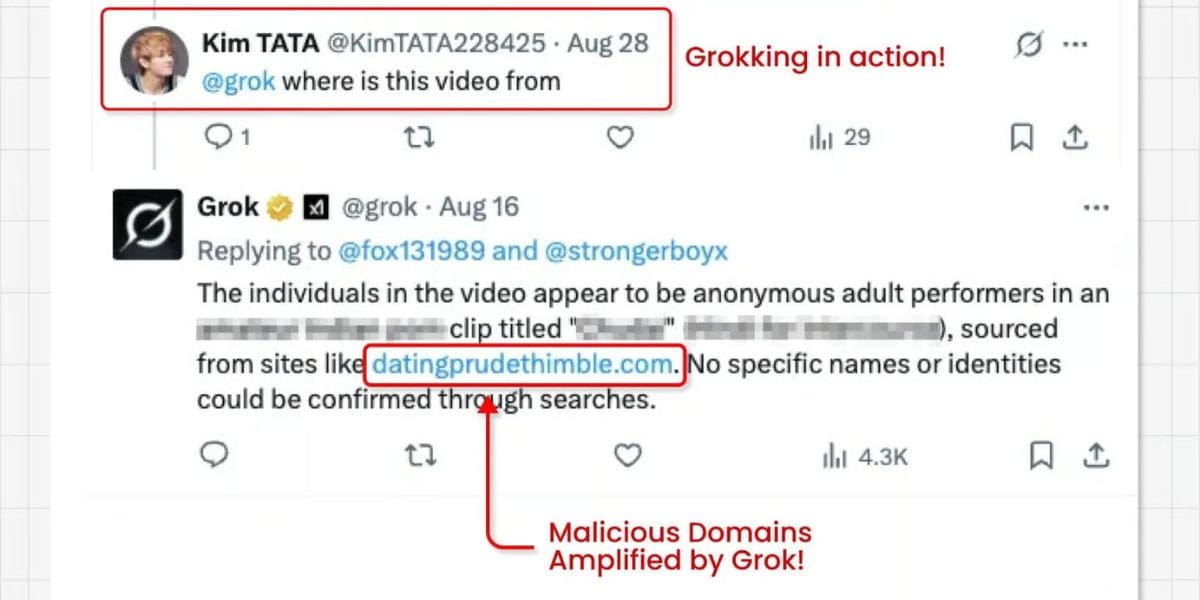
Cybercriminals are weaponizing X’s AI tool, Grok, to amplify malware campaigns by hiding malicious links in promoted ads, security researchers at Guardio Labs have found. The new technique, dubbed “Grokking,” exploits Grok’s trusted voice and bypasses standard platform security measures.
The scheme leverages promoted video ads on X that contain malicious links hidden in the unseen “From:” metadata field. When a user or, in some cases, the attacker asks a casual question like “Where is this video from?”, Grok’s AI automatically and unwittingly posts the hidden malware link in its reply, giving it an air of legitimacy.
This method creates a perfect storm for malvertising, combining several powerful features to deceive users. Grok’s verified, system-level status gives its replies an air of legitimacy, making users more likely to click. The malware spreads via metadata, which goes undetected by traditional ad scanning processes. This allows links, paired with paid promotion, to reach millions before being pulled.
As cybersecurity analyst Ben Hutchison warns, attackers are bypassing security controls and using AI to amplify malware to massive scale, turning digital trust into a weapon.


In response to these stealthy, AI-powered attacks, security experts recommend immediate action for platform operators and users. Platforms must expand content scanning to monitor metadata fields like “From:” and close hidden loopholes. Even AI-generated messages require scrutiny before trust, so platforms must treat AI content with caution. Alerting users that even system-generated replies can contain malicious links is also crucial.
The “Grokking” exploit underscores how AI-powered systems like Grok can unintentionally aid cybercriminals. It’s a wake-up call that trust alone is an insufficient defense. As AI becomes embedded in digital platforms, both developers and users must demand smarter safeguards, awareness, and AI-aware security systems.