A Chrome extension promoted as a free VPN service, and even carrying a verified badge in the store, has been caught doing the opposite of what users expected. Instead of protecting people’s privacy, it was silently capturing what appeared on their screens and sending the data elsewhere. As per KoiSecurity, more than 100,000 people had installed it by the time researchers uncovered what was happening.
How it unfolded
FreeVPN.One was not a sudden arrival. It had been in the Chrome Web Store for years, mostly unnoticed, operating as a straightforward tool. That changed in 2025. A sequence of updates pushed it far from its original function. In April, a new permission allowed it to see every site a user opened. Two months later, an update introduced scripting rights, supposedly to improve security. Then, in July, came the turning point, hidden screenshot capture built directly into the extension.
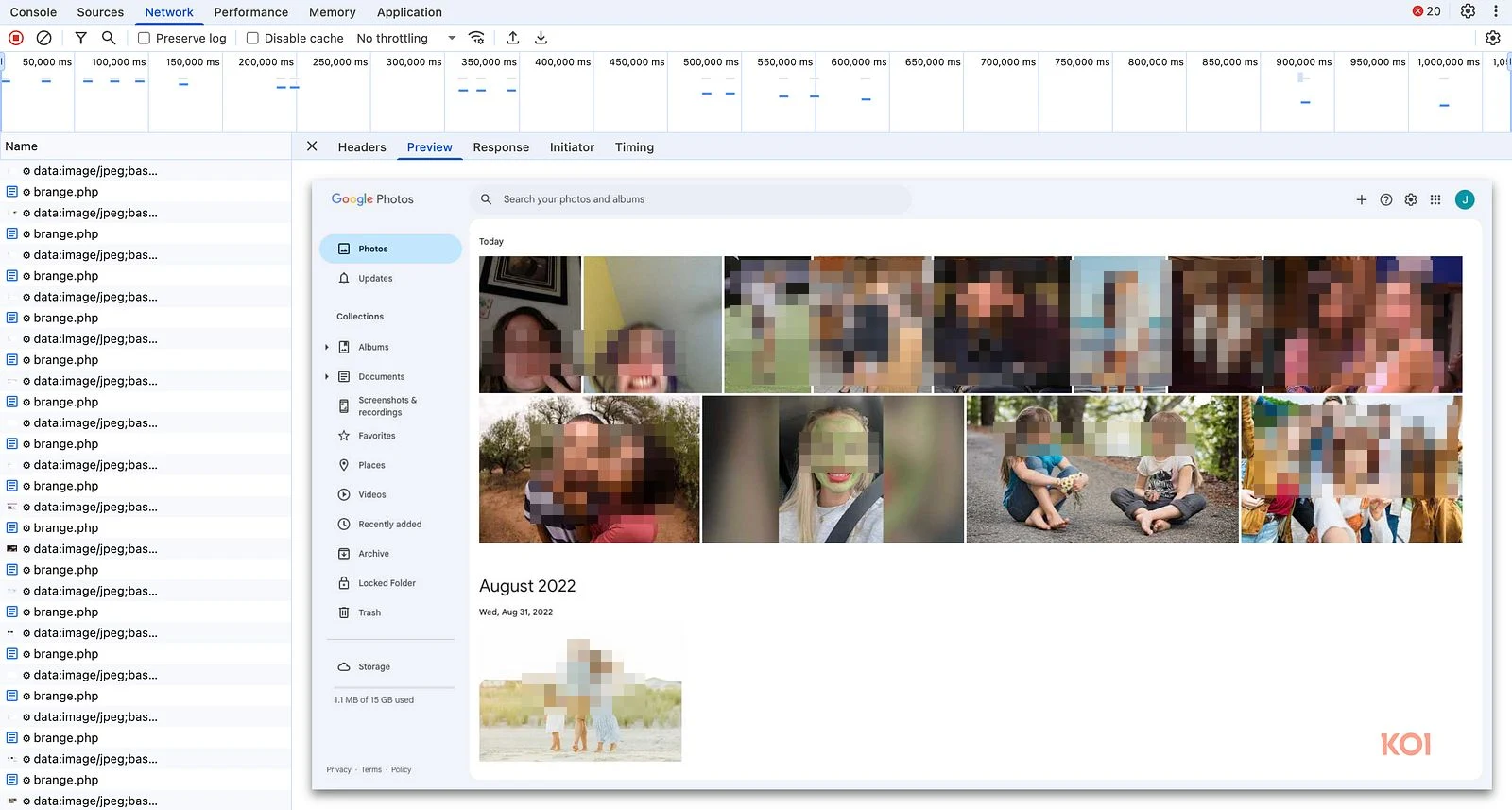
What this meant in practice was simple: each time a web page loaded, the extension paused for a moment, let the content render, then grabbed a snapshot of the visible tab. That image, combined with details like the web address, the tab identifier, and a unique number tied to the user, was quietly sent off to a remote server. No alert. No visible sign that anything had happened.
What was at stake
Screenshots don’t just show browsing activity; they show everything. A bank login form half-filled with account details. A company spreadsheet opened in a cloud service. Private photos in an online gallery. Even personal messages sitting in a chat window. All of it can be frozen in an image and transmitted in seconds, without the user ever knowing.

Later versions of the extension made the transfers harder to spot by encrypting the traffic with AES-256-GCM and RSA key wrapping. The encryption didn’t make the behavior less invasive, it simply disguised it so network monitoring tools would struggle to distinguish it from normal, legitimate connections.
More power than a VPN needs
A genuine VPN extension only needs a narrow set of permissions to function, mainly proxy handling and storage. FreeVPN.One demanded more. It asked to interact with all tabs, to run scripts on every website, and to read every URL visited. Each permission on its own might raise eyebrows. Taken together, they created the basis for round-the-clock monitoring.
One feature made the spying less obvious. The extension displayed an option labelled “AI Threat Detection.” That button, when pressed, warned that screenshots and URLs might be uploaded for checking. And indeed, when clicked, it sent data for analysis. The difference is that, behind the scenes, it was already doing the same thing constantly, whether the button was pressed or not.
The developer’s stance
When researchers reached out, the developer argued that the screenshot capture was part of background scanning designed to protect against harmful domains. The evidence did not support that claim. Captures were recorded even on mainstream services such as Google Sheets and Google Photos, hardly suspicious sites. The developer said the images were analyzed briefly and not stored, but offered no proof.
Requests for company information or developer credentials went unanswered. The only contact point was a generic email, and the associated website resolved to a basic template page, giving no sign of a real organization behind the product.
Bigger questions about oversight
Despite the findings, the extension remained available in the Chrome Web Store at the time of reporting. That raises concerns about how well Google’s security checks actually work. In theory, both automated scans and human reviews are supposed to prevent malicious code from slipping through. In reality, a tool that shifted from VPN to spyware managed to stay listed, complete with a verified badge and prominent placement.
The lesson for users
This case illustrates a recurring problem. Extensions that appear free, useful, and even certified can, with a single update, transform into surveillance tools. Once broad permissions are granted, there is little visibility into what is happening in the background. And once sensitive information leaves a device — whether a password, a message, or a photograph — there is no way for a user to verify how it is being used.
What began as a VPN branded around privacy ended up functioning as a window into people’s digital lives. For those who installed it, the cost of a free service was hidden in plain sight.
Notes: This post was edited/created using GenAI tools.
Read next:
• Inside the Water Crisis of Data Centers: Google, Meta, and the Hidden Costs of AI Growth
• DeepSeek V3.1 Expands China’s AI Push With Open-Source Frontier Model