At the Black Hat security conference, a team from cyber-physical security firm Claroty presented findings from their study of cameras made by Axis Communications, a Swedish manufacturer used by governments, hospitals, schools, and major companies. These systems are designed for large deployments, often with hundreds of units across multiple locations, and remote access is part of their setup.

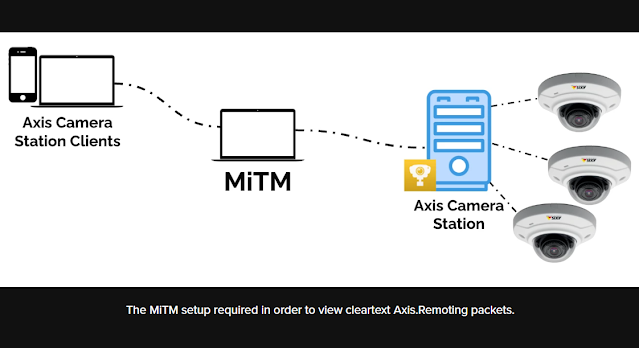
The team found that a specific remote service within some Axis camera systems could be reached over the internet. The company offers a more secure remote option that is costly, but many customers use a lower-cost version that leaves this service open. This exposure allowed the researchers to take control of connected cameras. Their access extended beyond the devices to the software used to manage them, meaning they could view, change, or disrupt any live or recorded footage.
The investigation showed that the flaw affected the cameras, the server software that coordinates them, and the client software used to view feeds. Each part could be controlled through remote commands once access was gained. In practical terms, the cameras function like small Linux-based computers, and the vulnerability allowed full administrative control over them.
Scanning the internet for exposed systems revealed more than 65,000 servers running the affected service, with thousands located in the United States. In some cases, the server names gave enough detail to identify the organisation operating them. This showed that many institutions had left systems accessible without realising the scale of the risk.
Axis Communications was notified about the flaw and produced an update to close it. The researchers noted that the company responded quickly and distributed the patch promptly. They also stressed that applying these updates is critical to keeping systems secure.
The case demonstrates that even trusted equipment can contain vulnerabilities. Regular updates and proper configuration remain essential for both large organisations and small installations. Security systems should be checked as often as they are used, because new flaws can be found at any time.
Notes: This post was edited/created using GenAI tools. Image: DIW-Aigen.
Read next: Palestinians in Gaza Struggle to Keep Fundraising Accounts Alive on Bluesky