Security researchers report over 15,000 websites designed to look like TikTok Shop, TikTok Mall, or TikTok Wholesale. These sites display polished visuals, fake reviews, and branding similar to official TikTok services. Victims often arrive through sponsored ads on TikTok, Facebook, Telegram, or WhatsApp. Many of the ads show familiar faces and product discounts that appear convincing but are fabricated.
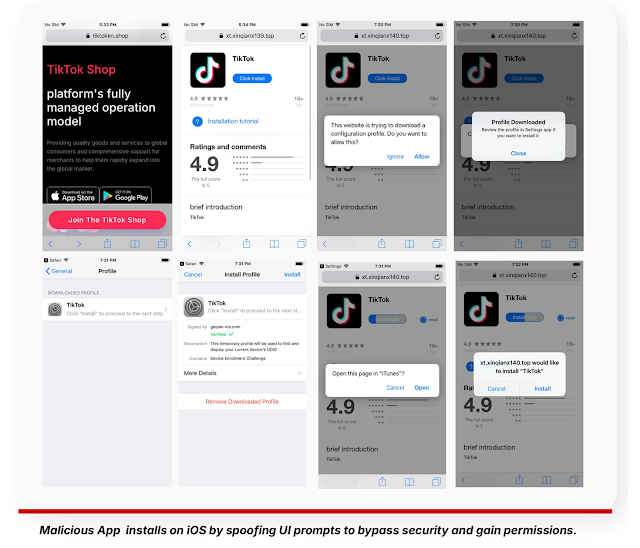
Some users are asked to log in to these fake storefronts. Others are prompted to download a mobile app that looks identical to TikTok’s. The app, once installed, behaves like the real one but runs spyware in the background. This spyware, called SparkKitty, collects personal data and sends it to external servers under attacker control.

The apps are distributed through links and QR codes, not through official app stores. Researchers have found more than 5,000 separate sites offering these downloads.
Login pages on these sites sometimes produce an error after users enter their credentials. The app then asks for a Google login instead. This method uses a token system that attackers can exploit to gain access without needing the original password.
The scam extends to financial theft. Victims are asked to send payments using cryptocurrency, often through a wallet page built into the fake store. Some are shown dashboards that display fake earnings, prompting them to send additional funds under the impression they will receive a payout. These balances are fake, and no returns are issued.
The scammers use domain extensions like .shop, .top, and .icu to build out their network. These are cheaper to register and less likely to trigger automated alerts. The tactic allows the campaign to spread across regions that TikTok Shop does not officially support.
Researchers emphasize that TikTok’s real platform and affiliate program operate through the official tiktok.com domain. Any site that requests payments up front, asks for login details outside official apps, or promotes offers that look unrealistic should be treated with suspicion.
The scope of this operation shows how trust in familiar brands can be used against users. The tools involved, malware, cloned websites, spoofed identities, have been built to avoid detection and scale quickly. The scam remains active, and new variants continue to appear.
Notes: This post was edited/created using GenAI tools.
Read next: WhatsApp Bans Millions of Scam Accounts, Adds New Safety Alerts