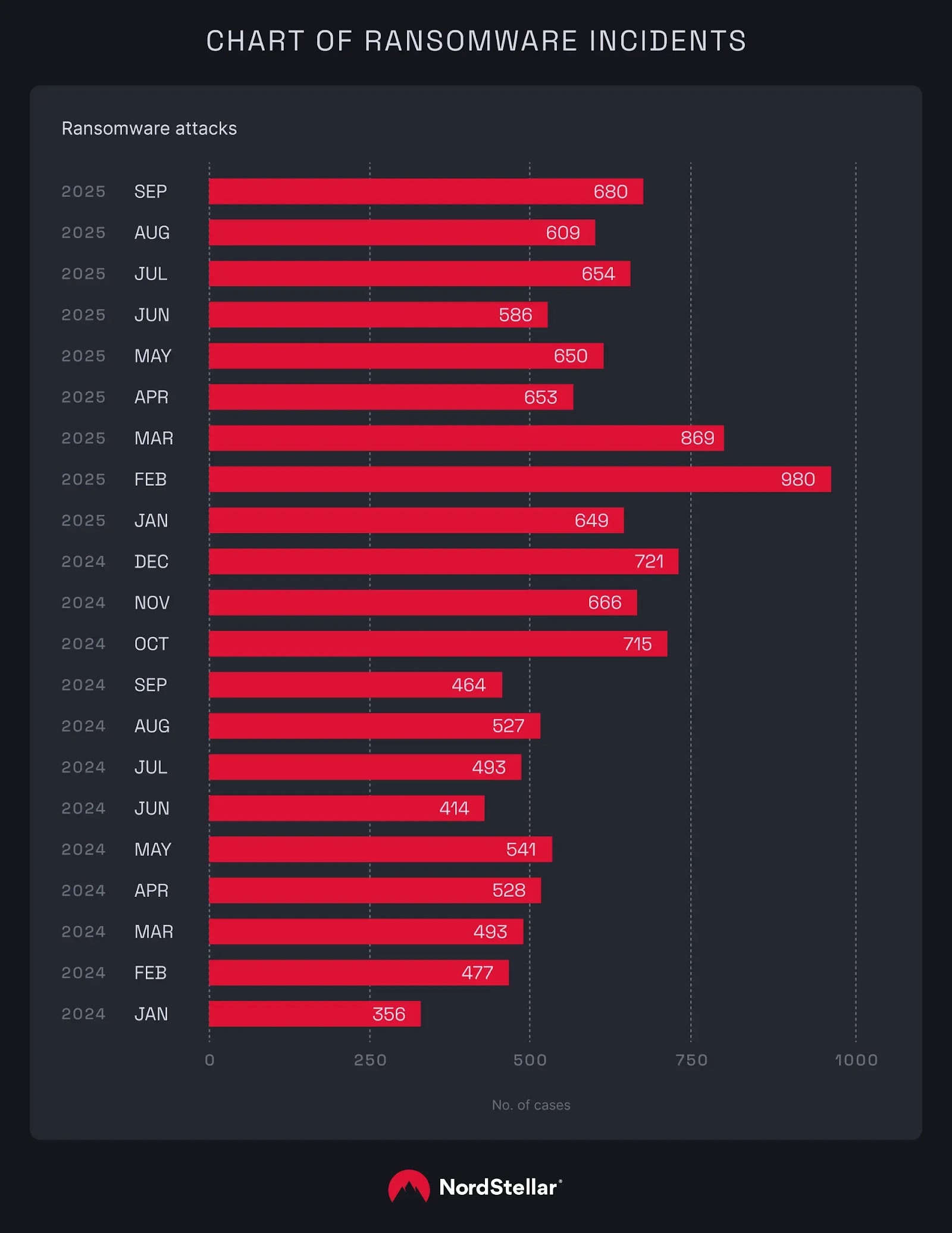
Ransomware activity has risen sharply in 2025, with cybercriminals striking thousands of companies worldwide and US-based firms facing the heaviest losses.
US Firms Remain the Primary Targets
The United States accounted for more than half of all identifiable incidents in the third quarter, recording 686 cases out of about 1,274 where victim locations were confirmed. Canada, Germany, the United Kingdom, and France followed at a distance. Analysts link this concentration to the large number of public and profitable businesses based in the US, coupled with regulatory pressure that often pushes companies to settle incidents swiftly to limit operational damage.
Manufacturing Tops the List of Affected Industries
The manufacturing sector suffered the most in recent months, with 245 reported cases between July and September. High production costs and dependence on complex supply chains make manufacturers more vulnerable, especially when older systems remain unpatched or rely heavily on third-party vendors.
Smaller Companies Face Growing Risk
Small and medium-sized businesses continue to be prime targets, particularly those with fewer than 200 employees and annual revenues between $5 million and $25 million. Limited cybersecurity budgets and less-developed IT infrastructure make them easier to infiltrate. Many lack the resources to investigate incidents thoroughly or report them to authorities.
Ransomware Gangs Behind the Spike
Longstanding criminal groups continue to dominate the ransomware landscape. The Qilin syndicate led activity in the third quarter with more than 240 incidents, followed by Akira, INC Ransom, Play, and Safepay.
How Companies Can Strengthen Defenses
NordStellar’s data suggests that the persistence of ransomware reflects how profitable the model remains. Many organizations, even after paying the ransom, struggle to regain full access to their systems or risk facing a second demand.
A Continuing Battle
The upward trend in ransomware attacks shows little sign of slowing. With over 1,900 incidents recorded in the third quarter alone, 2025 is shaping up to be one of the most active years for ransomware on record.
References
- ^ NordStellar (nordstellar.com)