The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added[1] a high-severity security flaw impacting Smartbedded Meteobridge to its Known Exploited Vulnerabilities (KEV[2]) catalog, citing evidence of active exploitation.
The vulnerability, CVE-2025-4008[3] (CVSS score: 8.7), is a case of command injection in the Meteobridge web interface that could result in code execution.
“Smartbedded Meteobridge contains a command injection vulnerability that could allow remote unauthenticated attackers to gain arbitrary command execution with elevated privileges (root) on affected devices,” CISA Said.
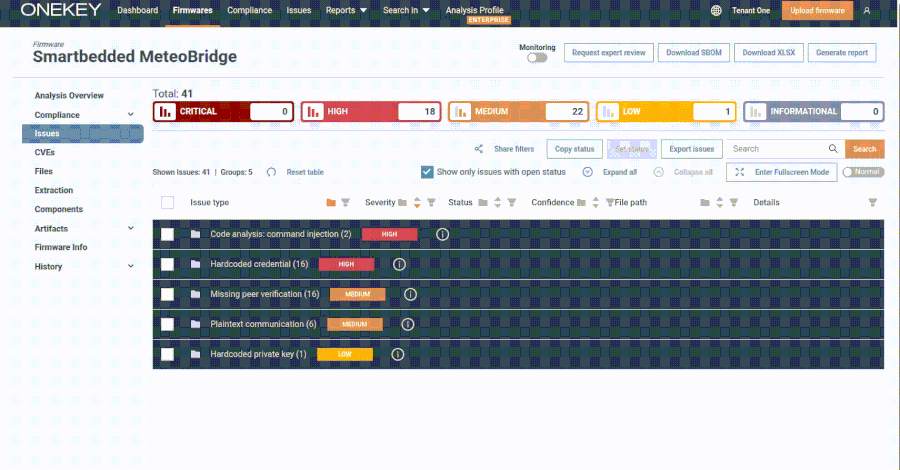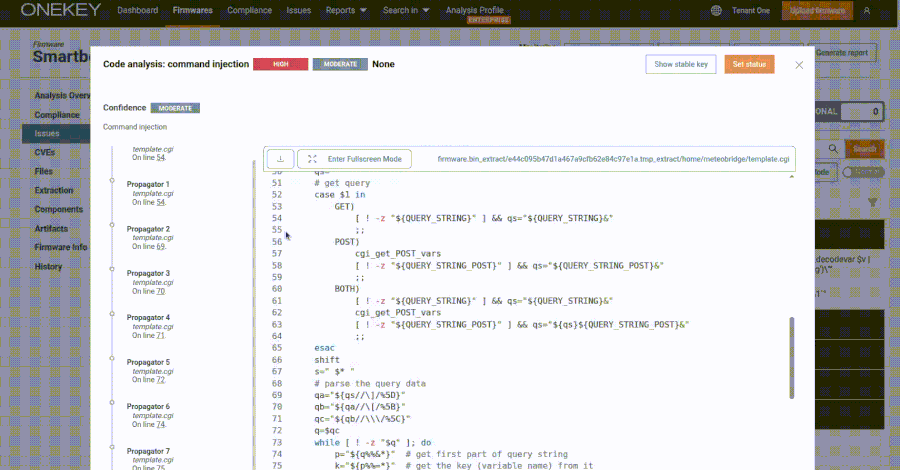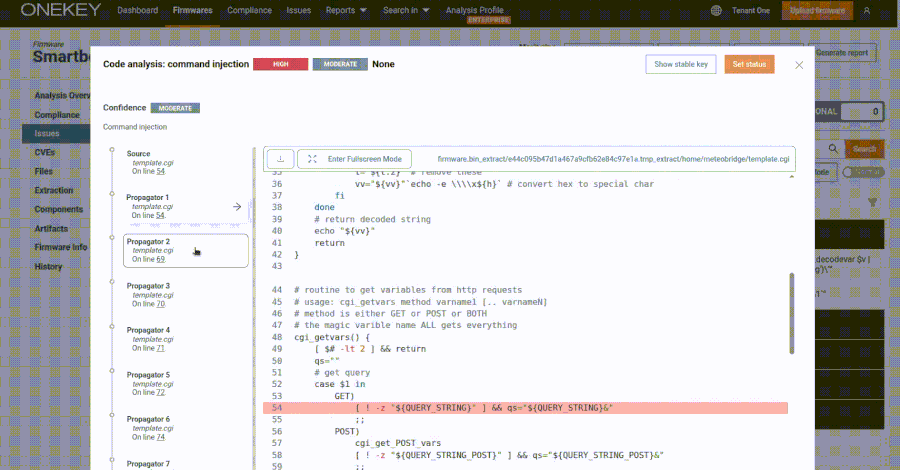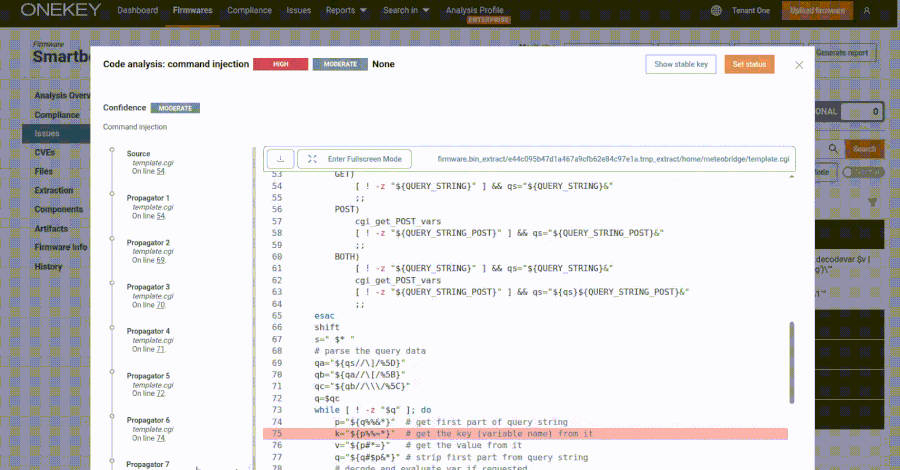
According to ONEKEY, which discovered and reported[4] the issue in late February 2025, the Meteobridge web interface lets an administrator manage their weather station data collection and control the system through a web application written in CGI shell scripts and C.
Specifically, the web interface exposes a “template.cgi” script through “/cgi-bin/template.cgi,” which is vulnerable to command injection stemming from the insecure use of eval calls, allowing an attacker to supply specially crafted requests to execute arbitrary code –
curl -i -u meteobridge: meteobridge
'https://192.168.88.138/cgi-bin/template.cgi?$(id>/tmp/a)=whatever'Furthermore, ONEKEY said the vulnerability can be exploited by unauthenticated attackers due to the fact that the CGI script is hosted in a public directory without requiring any authentication.
“Remote exploitation through a malicious webpage is also possible since it’s a GET request without any kind of custom header or token parameter,” security researcher Quentin Kaiser noted back in May. “Just send a link to your victim and create img tags with the src set to ‘https://subnet.a/public/template.cgi?templatefile=$(command).'”
There are currently no public reports referencing how CVE-2025-4008 is being exploited in the wild. The vulnerability was addressed[5] in Meteobridge version 6.2, released on May 13, 2025.
Also added by CISA to the KEV catalog are four other flaws –
- CVE-2025-21043[6] (CVSS score: 8.8) – Samsung mobile devices contain an out-of-bounds write vulnerability in libimagecodec.quram.so that could allow remote attackers to execute arbitrary code.
- CVE-2017-1000353[7] (CVSS score: 9.8) – Jenkins contains a deserialization of untrusted data vulnerability that could allow unauthenticated remote code execution, bypassing denylist-based protection mechanisms.
- CVE-2015-7755[8] (CVSS score: 9.8) – Juniper ScreenOS contains an improper authentication vulnerability that could allow unauthorized remote administrative access to the device.
- CVE-2014-6278[9], aka Shellshock[10] (CVSS score: 8.8) – GNU Bash contains an OS command injection vulnerability that could allow remote attackers to execute arbitrary commands via a crafted environment.
In light of active exploitation, Federal Civilian Executive Branch (FCEB) agencies are required to apply the necessary updates by October 23, 2025, for optimal protection.
References
- ^ added (www.cisa.gov)
- ^ KEV (www.cisa.gov)
- ^ CVE-2025-4008 (nvd.nist.gov)
- ^ discovered and reported (www.onekey.com)
- ^ addressed (forum.meteohub.de)
- ^ CVE-2025-21043 (thehackernews.com)
- ^ CVE-2017-1000353 (nvd.nist.gov)
- ^ CVE-2015-7755 (nvd.nist.gov)
- ^ CVE-2014-6278 (nvd.nist.gov)
- ^ Shellshock (thehackernews.com)