In the last two years, the boom of artificial intelligence has resulted in an arms-race in computing power, graphics performance, and consumer hardware. While on the surface this sounds like a beneficial thing, there is also a flip side. This artificial intelligence boom is also benefiting cybercriminals who aim to hack passwords better, faster, and more efficiently. With new generation hardware, such as Nvidia’s recent 50-series and AMD’s upcoming transition to ‘UDNA’ architecture, high-quality computing is becoming more affordable and more available. From this, the burden of entry for cybercriminals is reduced and hackers are able to run computations to crack passwords much faster and much more often.
What is Password Hashing?
It is a relatively standard protocol that enterprises protect their user’s passwords with hashing algorithms. Storing passwords as plain text is considered a bad practice, because anyone who can access a database – authorized or unauthorized – can simply read the passwords and take them if they so wish. Hashed passwords, however, aim to prevent people from being able to read the passwords. Think of hashed passwords as a mask on the true thing. The only way for people to know the true password beneath the mask is if each password is individually unscrambled through brute force techniques.
Brute force hacking is when hackers, with the assistance of quality hardware, guess possible password combinations through a series of trial and error guesses. Individually, this would be impractical due to how long it would take to go through every possible combination, however, now with access to such powerful hardware, hackers can run billions of these computations simultaneously, and thus faster.
The Bcrypt Hashing Algorithm
There are many different types of hashing algorithms, some of which are better than others. MD5, for example, is older and not as effective. It is hence frequently cited as one of the most common hash algorithms found in leaks, demonstrating its lack of efficacy.
Bcrypt is another hashing algorithm, developed in 1999. This one turns a user’s password into a string of characters in a one-way hashing function which is irreversible, meaning that it cannot be changed back to the original password. When a user logs in, this algorithm re-hashes the password and compares the value to the one already stored in the system memory to see if the passwords match. If the password is short to begin with, the bcrypt hashing process also can stretch it to become longer and more complex. Bcrypt also adds a random piece of data to each password hash, ensuring uniqueness. This increases the difficulty that passwords[1] can be guessed with dictionaries or brute-force attacks, and is also known as salting where a 22-character string is put in front of the hash.
What differentiates bcrypt hashing from other algorithms is also that it has a cost factor to it. This shows how many password iterations were made before the hash is generated and is applied in front of the salt, thus significantly increasing the time, effort, and resources required to calculate the password.
How Does Bcrypt Stand Up Against New Generation Hardware?
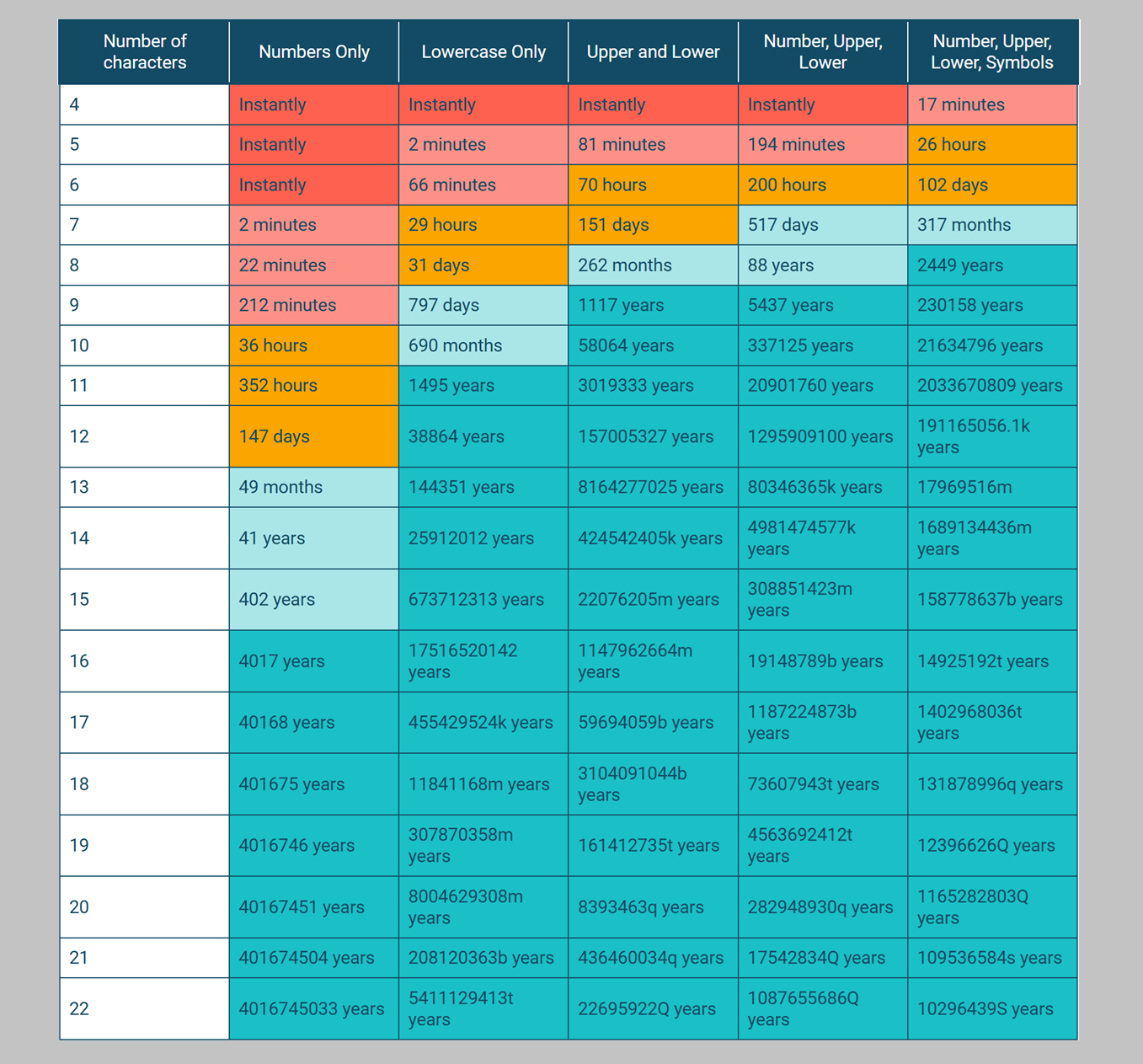
While bcrypt hashing is generally considered effective, the boom of artificial intelligence and the increased affordability, capability and availability of new generation hardware has only improved the performance of brute force hacking techniques against hashed passwords and data sets. In a recent study[2] by Specops Software, researchers used newer, more powerful hardware to determine how long exactly it takes to crack bcrypt. These findings were compared to a similar study[3] from two years ago, with weaker hardware to show exactly how fast hackers are advancing alongside the hardware they use.
In the Specops Software study, a sample of 750,000 hashes was taken from well-known data leaks (RockYou2024, etc.), and put under the pressure of brute force hacking techniques. The findings showed that the mass investment in artificial intelligence infrastructure by major enterprises has significantly increased the availability of heavy compute hardware. A couple of years ago, one might expect that brute force attacks would be conducted by hardware like the RTX 4090 graphics card. But today’s RTX 5090 flagship cards are approximately 65% faster when up against bcrypt hashing.
The findings of the study found that short, non-complex passwords were able to be cracked relatively quickly by both older, less powerful hardware and with new generation artificial-intelligence powered hardware. Passwords like ‘password’, ‘123456’, ‘admin’, and the like have always been easily crackable, even in the beginning of the internet. Unfortunately, these passwords remain very commonly used even to this day. This is because a lot of users, both in and out of the workplace, experience password fatigue from all the different, unique credentials they must remember for all their different accounts.
However, even so, the newer hardware was able to crack slightly more complex passwords much faster. The older study found that bcrypt hashed passwords with 6 or 7 characters that were made of numbers only could be cracked instantly. The new generation hardware, however, was able to instantly crack hashed passwords of 4 to 6 characters including numbers, uppercase, and lowercase.
Password Best Practices
From the study’s findings, we can conclude that the longer, more-complex the password, the better. As complexity increases, so too does the length of time it takes to crack a hashed dataset. Indeed, once a password becomes over 12 characters long, with a combination of types of characters, the time to crack becomes nearly impossible for hackers.
For this reason, it is important that individuals and organizations always follow a few key practices to ensure a combination of protections. Passwords should ideally be at least 18 characters and they should also always be comprised of each of the following: lowercase, uppercase, numbers, and special characters.
Additional protections include enabling passphrases with at least 18 characters and including multiple or all character cases (uppercase, lowercase, digits, and special characters). Complexity in passphrases goes against advice since length is key over complexity, but this will make the phrase harder to crack. It’s recommended to avoid lines from songs, poems, and films, and deliberately misspelling a word can be good practice. Organizations may also implement a custom dictionary for their employees which blocks words that are associated with the organization itself, such as words in the company name or products.
The Problem: Known, Compromised Passwords
Implementing strong password protocols is the first step to protecting against the brute force hacking of passwords. However, it is important to understand that once an attacker already has access to a password or dataset in question – whether because of re-use or because it has been leaked through infostealers – it becomes too late. In this case, it does not matter how complex a password is or how well it has been hashed. If someone in an organization reuses passwords across multiple accounts, then their single compromised password could be the difference between an entire company being hacked or not.
Complex hashing protocols should never be considered a replacement for good password security hygiene. In order to maintain good password security hygiene, passwords should be unique and never reused. The Specops Software study, after all, found that the time to crack known, compromised passwords was instantaneous, regardless of the kind of hardware that was used, and regardless of how well it was hashed. In order to prevent risk, organizations and individuals must continuously be aware of appropriate password hygiene, they must never allow the re-use of passwords, and they must constantly be on guard that their passwords do not become compromised.
Darren James is a Senior Product Manager at Specops Software , an Outpost24 company. Darren is a seasoned cybersecurity professional with more than 20 years of experience in the IT industry. He has worked as a consultant across various organizations and sectors, including central and local governments, retail and energy. His areas of specialization include identity and access management, Active Directory, and Azure AD. Darren has been with Specops Software for more than 12 years and brings his expertise to the support and development of world-class password security and authentication solutions.[4]
Read next: AI Chatbots Use Emotional Pressure to Keep People From Logging Off[5]
References
- ^ increases the difficulty that passwords (www.digitalinformationworld.com)
- ^ study (specopssoft.com)
- ^ study (specopssoft.com)
- ^ Specops Software (specopssoft.com)
- ^ AI Chatbots Use Emotional Pressure to Keep People From Logging Off (www.digitalinformationworld.com)