- FastNetMon detected record 1.5 billion packet per second DDoS attack
- Traffic came from hijacked IoT devices and MikroTik routers across 11,000 networks
- FastNetMon warns ISP level filtering is essential to stop future large scale floods
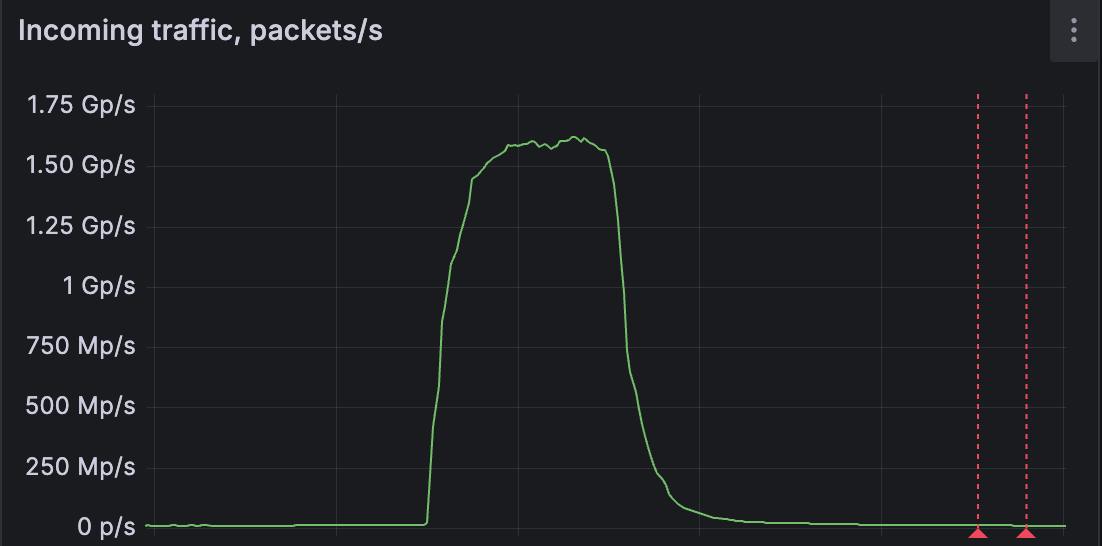
A distributed denial-of-service attack targeting a DDoS mitigation vendor somewhere in Western Europe has been spotted and mitigated by FastNetMon[1].
The firm says the attack peaked at a massive 1.5 billion packets per second, making it one of the largest packet-rate floods confirmed to date.
FastNetMon says that the traffic was mainly a UDP flood sourced from compromised customer-premises equipment, including IoT devices and MikroTik routers.

Part of a dangerous trend
The attack reportedly drew on resources from more than 11,000 unique networks worldwide.
The targeted company wasn’t named, although FastNetMon described it as a DDoS scrubbing provider, a type of service that filters out malicious traffic during these type of attacks.
“This event is part of a dangerous trend,” said Pavel Odintsov, founder of FastNetMon. “When tens of thousands of CPE devices can be hijacked and used in coordinated packet floods of this magnitude, the risks for network operators grow exponentially. The industry must act to implement detection logic at the ISP level to stop outgoing attacks before they scale.”
The attack was detected and handled in real time, with FastNetMon’s systems automatically identifying the abnormal traffic within a matter of seconds.
Mitigation efforts relied on the scrubbing technology at the customer’s facility and involved deploying access control lists on routers known to be vulnerable to amplification techniques.
FastNetMon says its platform is designed to process events at this scale by using optimized C++ algorithms to provide visibility into network traffic.
The quick action allowed the attacked company to withstand the onslaught without any visible disruption to its service.
This announcement follows Cloudflare’s recent disclosure of a record-breaking volumetric attack that reached 11.5Tbps and 5.1 billion packets per second.
“Taken together, the two incidents underline a rise in both packet-rate and bandwidth-driven floods, a trend that is pressuring the capacity of mitigation platforms worldwide,” FastNetMon said.
“What makes this case remarkable is the sheer number of distributed sources and the abuse of everyday networking devices. Without proactive ISP-level filtering, compromised consumer hardware can be weaponized at a massive scale,” the company warned.
You might also like
References
- ^ FastNetMon (fastnetmon.com)