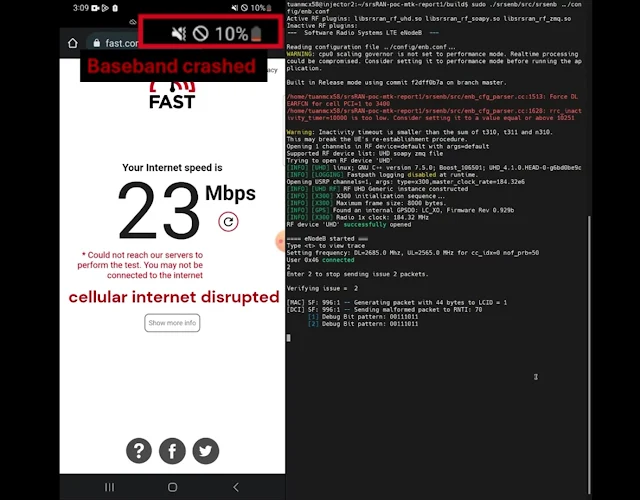
Low-Level Modem Layers Exposed to Signal Attacks
The flaw lies deep in the baseband processor. That’s the chip inside phones that controls wireless communication with nearby cell towers. Unlike the phone’s operating system, which handles apps and interface elements, the baseband runs a separate set of processes. These are responsible for connecting, maintaining, and routing cellular signals. Researchers at KAIST and Kyung Hee University built a custom tool called LLFuzz to test how baseband chips react to malformed signals. This tool generates wireless packets and sends them over the air using a laptop and a software-defined radio. In lab conditions, they tested the tool against 15 different smartphones. Their results showed that a single radio packet could crash the modem in many devices. When the malformed packet was sent, the phone’s data connection shut down instantly. The researchers recorded video showing phones streaming data, then freezing when hit by the signal.
Multiple Vendors Affected Across Device Tiers
The testing revealed flaws in devices from Apple, Samsung, Google, and Xiaomi. These phones use modem chips from Qualcomm, MediaTek, Samsung, and Apple. Altogether, the researchers found 11 separate vulnerabilities. Seven of them were given official CVE identifiers. Security patches have been issued for most of these. Four more are still under review or not yet disclosed. The vulnerabilities affect chips across price ranges. Entry-level smartphones, tablets, smartwatches, and internet-of-things gadgets all use the same families of baseband processors, which puts a wide number of devices at risk. Even the newest chipsets, like Samsung’s Exynos 2400, were found to contain the flaws.
Baseband Layers Often Lack Encryption or Authentication

Image: KAIST
The attacks targeted the lower layers of the modem stack—known as MAC, RLC, PDCP, and PHY. These layers handle tasks such as how data is split into packets, how it’s scheduled for transmission, and how it’s delivered. Unlike higher layers that are often encrypted or checked for integrity, these lower ones often accept raw radio signals without filtering. This means the modem could be tricked just by receiving a malformed packet at the right time. In some cases, attackers wouldn’t need to crack any encryption or perform advanced spoofing. If the modem accepts the signal, it might crash or behave unexpectedly.
Standard Network Tests Don’t Catch These Issues
Current mobile testing standards focus on conformance checks. These tests confirm that phones respond correctly to regular network traffic. But they don’t test how modems handle irregular or malformed signals. As a result, flaws in rarely used or edge-case packet structures go unnoticed. The LLFuzz tool was designed to fill that gap. It maps out the various states a modem can be in, then sends crafted packets designed to target those states. This includes less common configurations that don’t appear in typical mobile traffic. During the experiments, researchers discovered bugs that could be triggered during network attach procedures and after authentication was completed.
Some Attacks Can Happen After Secure Login
Many of the found flaws occur after the phone has authenticated with the network. That means even if encryption is active at higher levels, the modem’s lower functions can still be exploited. The researchers explained that these vulnerable layers remain exposed to airwave signals, even in secure sessions. The affected devices processed these malicious packets as if they were regular messages. This led to denial of service in most cases. But some of the issues could open paths to deeper attacks, including memory corruption, which may allow code execution in future scenarios.
Tool to Be Shared Openly for Broader Security Checks
The team plans to release LLFuzz as an open-source tool. Their aim is to push for the creation of a standardized test framework for baseband modems. The team argues that since these chips play a core role in nearly every mobile device, their security must be held to stricter standards. They’ve already begun adapting the tool for 5G. In early trials, it uncovered additional bugs in modern networks, suggesting the same kinds of problems are likely still present in newer protocols. Their full research will be presented at USENIX Security 2025.
Read next: Walmart Tops Global 500 Again as U.S., China, and Tech Titans Dominate $41.7 Trillion List